Cytracom two factor authentication (2FA) allows users to increase control of how credentials are used to access their account. The Cytracom 2FA setup process requires use of a smartphone authentication app to generate a verification code which is a 6-digit time-based, one-time password (TOTP) which is typically only valid for 30 seconds.
Once 2FA is setup for a user, the same authentication credentials are enforced for access to:
- Portal (secure.cytracom.net)
- Desktop (desktop.cytracom.net)
2FA Setup Process Overview
- If you do not have an authentication app on your smartphone, then download one such as the Google Authenticator
- Log into the Cytracom portal at secure.cytracom.net to enable 2FA on the user profile.
- When presented with the Cytracom QR code, use your authentication app to scan in and register Cytracom in your authentication app.
- Confirm setup by entering the verification code from the authentication app.
2FA Setup Process Details
Goto the Cytracom Portal at secure.cytracom.net
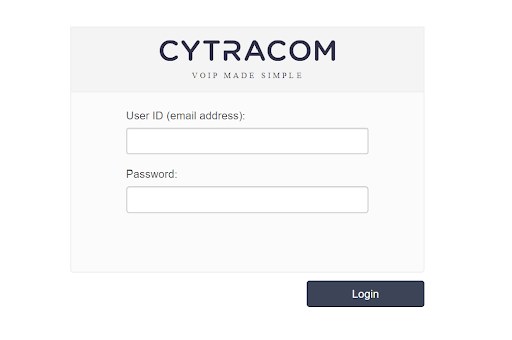
Enter user ID and password, then click "Login" to access the portal
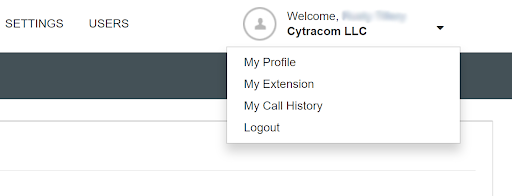
Select dropdown for user details to view options, and then select "My Profile" to view the user profile
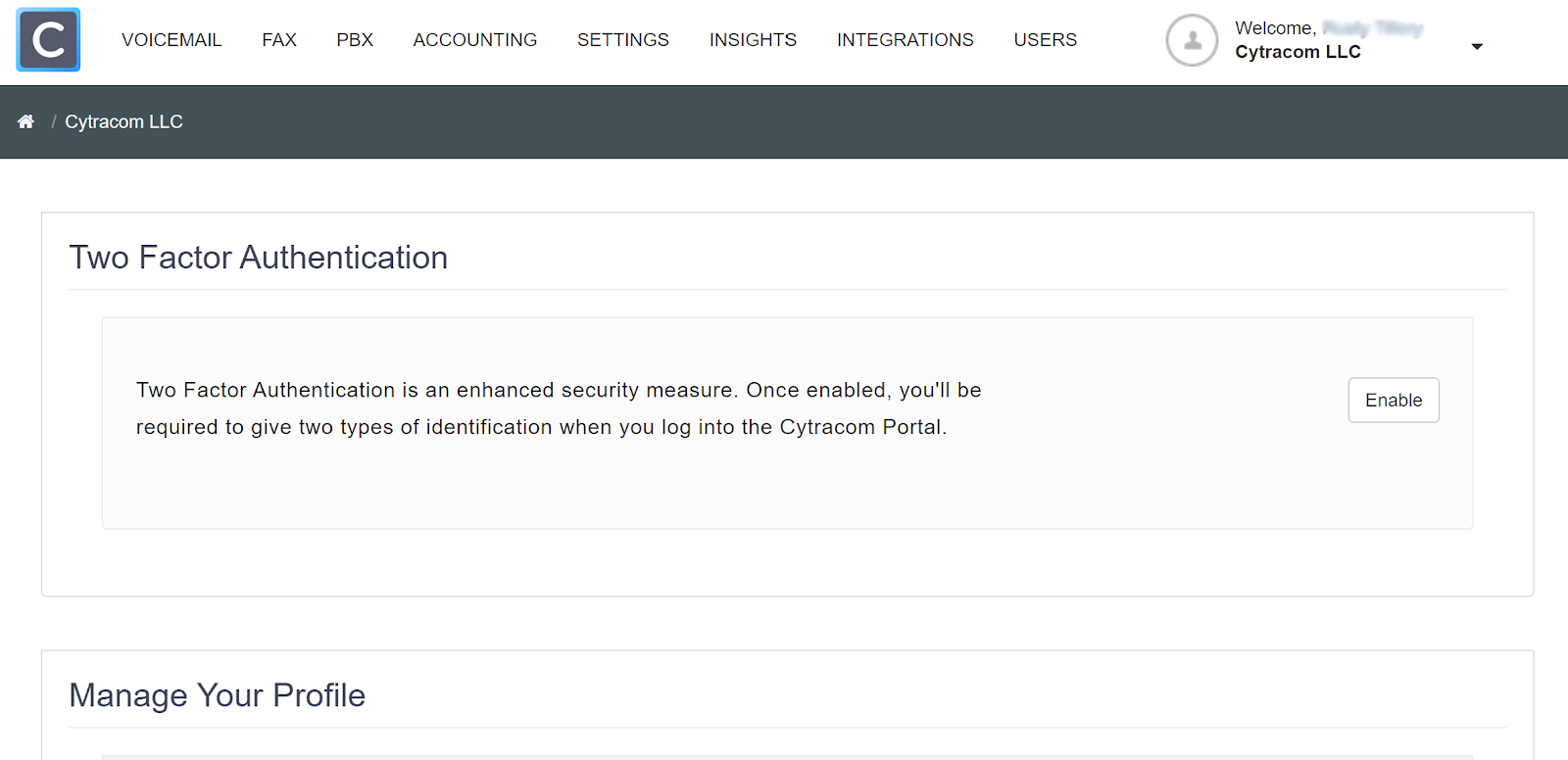
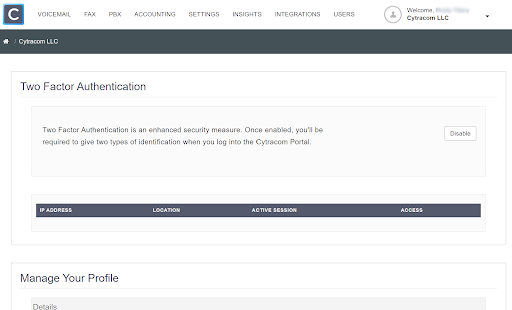
To setup Two Factor Authentication for the user, simply click "Enable" to begin the simple guided steps to:
- Register Cytracom with your authentication app by scanning QR code
- Verify the code from your authentication app
- Finish to acknowledge setup is complete
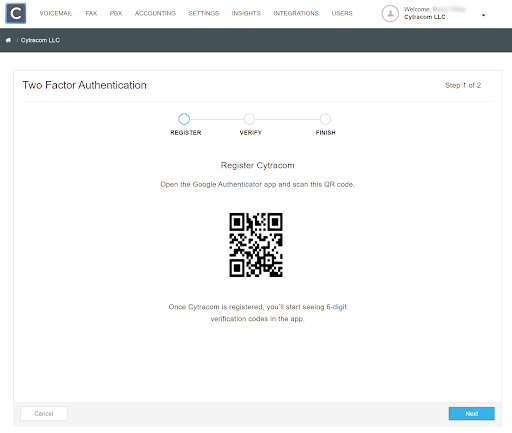
Use your authenticator app on your smartphone to scan the QR code to register Cytracom and begin generating the 6-digit one-time passwords. Once Cytracom is listed in the authentication app, proceed to the verification step in the Cytracom portal by clicking "Next".
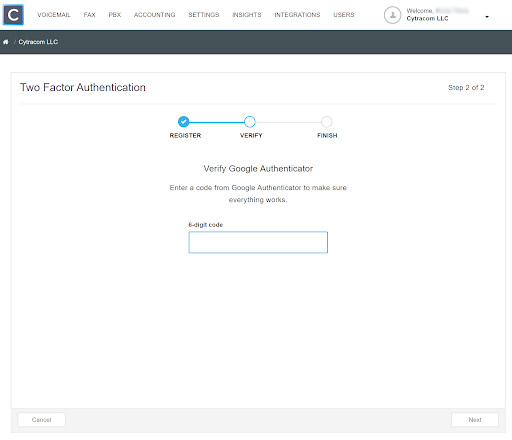
Find the current Cytracom verification code generated in the authentication app. Enter that verification code as the 6-digit code.
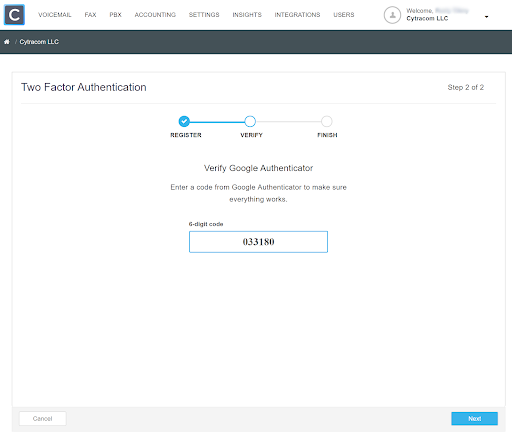
Clicking "Next" will finish the 2FA setup which makes the current login location a trusted location so you will not be prompted to enter the verification code when login is from that trusted location (IP Address).
If you happen to enter an invalid verification code, then you will be returned to the initial login screen to start the login again.
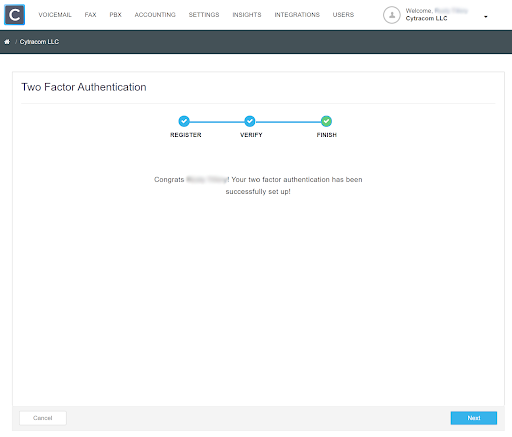
Acknowledge the process is finished by clicking "Next". The enabled 2FA now appears in the user profile with the option to disable.
2FA Login Without Trusted Location
A login from any IP address not set as a trusted location will prompt for the verification code and allow you to set the "Don't ask me again on this computer".
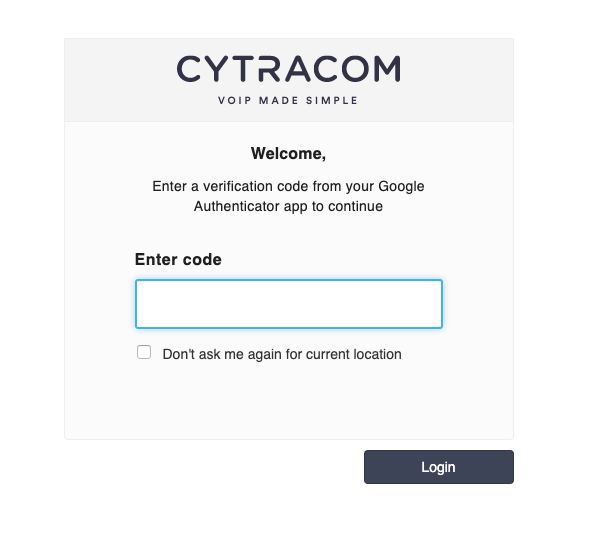
Find the verification code on your smartphone authentication app and enter it.
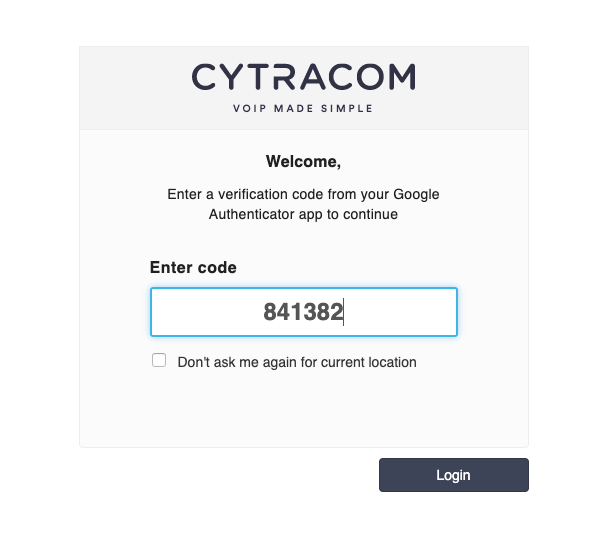
If you wish to establish the current location as trusted so that you will not be challenged to enter a verification code, then click the checkbox for "Don't ask me again for current location".
Simply click "Login" to access the portal.
Selecting the option to "not ask" results in the location being added to the list of trusted locations displayed in the two-factor authentication settings on the user profile.
Note that entering an invalid verification code will simply deny access and send you back to the initial login, but Congrats, you got it right and can see the trusted locations.
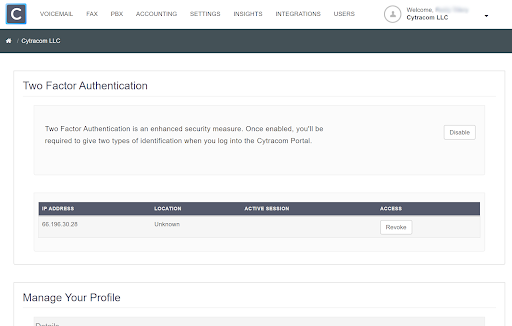
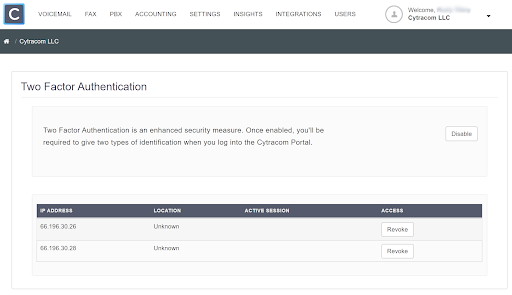
Revoke 2FA Trusted Location
To revoke a trusted location (IP Address), simply click "Revoke". Revoking a trusted location will result in a prompt of the challenge to enter the verification code when login is attempted by the user from that previously trusted IP address.
Revoking all the trusted locations allows 2FA to remain enabled, but will prompt the challenge to enter the verification code when login is attempted from any location.
Disable Two Factor Authentication
Simply click "Disable" to deactivate 2FA and return to single-factor authentication via a password.
Access Recovery
If the 6-digit verification code is somehow not available from the authentication app, an administrator can update the user's profile to disable two-factor authentication which will clear the previous 2FA credential. Simply enabling the user again will allow the setup to be repeated.
If the old Cytracom entry remains the authentication app, then it should be deleted since it will no longer generate valid verification codes. The entry producing the verification code which is successful in the validation step should be kept.
Note that previously trusted locations will remain for the re-enabled 2FA until they are specifically revoked.